IBM i SSL / TLS configuration and hardening guidelines.
Secure Socket Layer (SSL) / Transport Layer Security (TLS) protocols and Cipher Suites on IBMi are managed by a combination of
-
System Values QSSLPCL, QSSLCSLCTL, and QSSLCSL
-
Application definitions in Digital Certificate Manager
-
System Service Tool (SST) Advanced Analysis (AA) macro SSLCONFIG (IBM i 7.1, IBM i 7.2 & IBM i 7.3) or TLSCONFIG (IBM i 7.4)
Applications can negotiate secure sessions only with the protocols that are listed in IBM i system value QSSLPCL. If you set up QSSLPCL to TLSv1.2 then an application can perform SSL handshake using TLSv1.2 only.
To harden IBM i SSL/TLS, it is highly recommended to disable weak SSL/TLS protocols SSLv2, SSLv3, TLSv1.0, TLSv1.1 but does that make your IBM i SSL / TLS configuration completely secured? The answer is “NO” even though the IBMi (AS400) is a secure system.
To improve security you must remove NULL ciphers, EXPORT ciphers and weak ciphers in case they are explicitly specified in the system value QSSLCSL or implicitly when QSSLCSLCTL is set to *OPSYS. But before removing them system wide, careful planning is needed to ensure that no application or middleware are using these ciphers.
IBM i supports many Cipher Suites but default Cipher Suites list differs from release to release. You must review default cipher suites specific to your IBM i release and knock off weak Cipher Suites. Let us take an example of IBM i release 7.2 with its default Cipher Suites list. The default Cipher Suites list specifies NULL Ciphers, EXPORT Ciphers and Weak Ciphers. You must remove them to mitigate any known and potential security exploits. Vulnerability scanning would certainly report use of NULL Ciphers, EXPORT Ciphers and Weak Ciphers on your IBM i.
Default Cipher Suites on IBM i 7.4 no longer contain ECDSA_SHA224, ECDSA_SHA1, RSA_SHA224, RSA_SHA1, or RSA_MD5 signature algorithms. If the default Cipher Suites list is too restrictive for an application, then use Digital Certificate Manager to have an Application Definition with required Cipher Suites. At IBM i 7.4 default Cipher Suites list includes
-
AES_128_GCM_SHA256
-
AES_256_GCM_SHA384
-
CHACHA20_POLY1305_SHA256
-
ECDHE_ECDSA_AES_128_GCM_SHA256
-
ECDHE_ECDSA_AES_256_GCM_SHA384
-
ECDHE_RSA_AES_128_GCM_SHA256
-
ECDHE_RSA_AES_256_GCM_SHA384
IBM i and applications must use strong SSL / TLS protocols and strong Ciphers Suites but in in practice this is not the case. So, harden your SSL / TLS on IBM i in close coordination with what applications’ support using the listed sequence below.
-
Disable all Weak Cipher Suites: Table 1 below lists all weak Cipher suites.
-
Migrate applications not to use Cipher Suites that are common across TLSv1.2, TLSv1.1 and TLSv1.0 i.e.
-
*RSA_AES_256_CBC_SHA
-
*RSA_AES_128_CBC_SHA
-
*RSA_3DES_EDE_CBC_SHA
-
-
Update system value QSSLCSL to remove Cipher Suites common across TLSv1.2, TLSv1.1 and TLSv1.0
-
Order list of Cipher Suites from stronger to less strong or what is most commonly used by majority of your applications.
-
Update system value QSSLPCL to use TLSv1.3 and TLSv1.2. Do not leave QSSLPCL to *OPSYS as it enables weaker protocols by default in some IBM i releases. Details are listed in the table below as per the IBMi release.
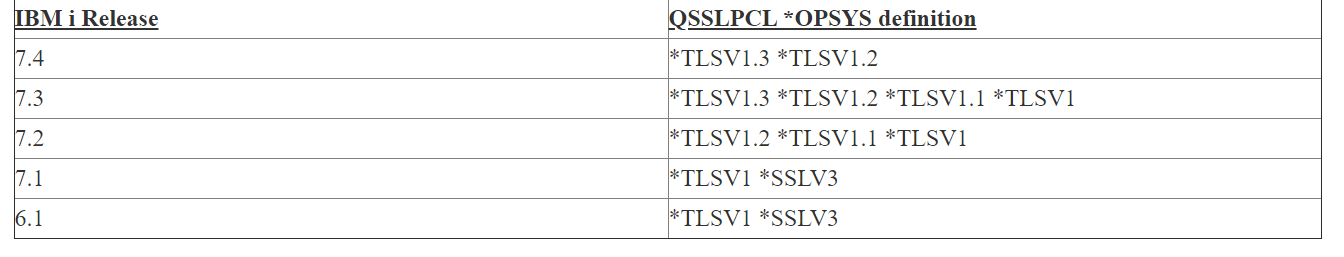
Table 1 - List of weak Cipher Suites
|
Cipher Suites |
TLSv1.3 |
TLSv1.2 |
TLSv1.1 |
TLSv1.0 |
SSLv3 |
SSLv2 |
|
*RSA_RC4_128_SHA |
|
X |
X |
X |
X |
|
|
*RSA_RC4_128_MD5 |
|
X |
X |
X |
X |
|
|
*RSA_NULL_MD5 |
|
X |
X |
X |
X |
|
|
*RSA_NULL_SHA |
|
X |
X |
X |
X |
|
|
*RSA_NULL_SHA256 |
|
X |
|
|
|
|
|
*RSA_DES_CBC_SHA |
|
|
X |
X |
X |
|
|
*RSA_EXPORT_RC4_40_MD5 |
|
|
|
X |
X |
|
|
*RSA_EXPORT_RC2_CBC_40_MD5 |
|
|
|
X |
X |
|
|
*RSA_RC2_CBC_128_MD5 |
|
|
|
|
|
X |
|
*RSA_DES_CBC_MD5 |
|
|
|
|
|
X |
|
*RSA_3DES_EDE_CBC_MD5 |
|
|
|
|
|
X |
|
*RSA_3DES_EDE_CBC_SHA |
|
X |
X |
X |
X |
|
|
*ECDHE_ECDSA_NULL_SHA |
|
X |
|
|
|
|
|
*ECDHE_ECDSA_RC4_128_SHA |
|
X |
|
|
|
|
|
*ECDHE_RSA_NULL_SHA |
|
X |
|
|
|
|
|
*ECDHE_RSA_RC4_128_SHA |
|
X |
|
|
|
|
|
*ECDHE_RSA_3DES_EDE_CBC_SHA |
|
X |
|
|
|
|
|
*ECDHE_ECDSA_3DES_EDE_CBC_SHA |
|
X |
|
|
|
|
Implementing and managing Security is needed for any system that is built for the future and IBMi is no exception.
Recent Posts
10 Reasons Why Small Businesses Need A CRM
February 1, 2023 | Business Development
Using Java on IBM i
May 18, 2021 | AS400/IBMi
FlashCopy versus Safeguarded Copy
April 28, 2021 |
Time to move to IBM i SMBv3
April 21, 2021 |
Search
Subscribe To Our Newsletter
Join our mailing list to receive the latest news and updates from our team.
